Cybersecurity. It is a term you have most likely heard with increasing frequency. It can seem a bit ominous and a bit nebulous. So what does it mean and why should we care about it?
Cybersecurity revolves around the protection of digital information. As our lives have become increasingly digital, the volume of online data points related to our personal information has grown. Information that once used to be housed only at select organizations (banks, government entities) is now right on your computer – think of all the online services and subscriptions you have signed up for, and all the devices you own connected to the internet.
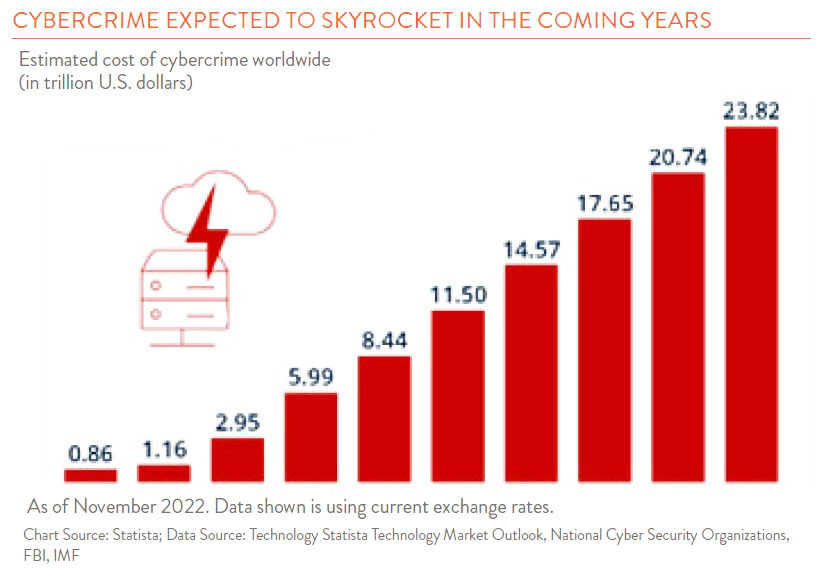
There are many positives to this ongoing digital transformation, but the glaring downside is the threat from those who want to exploit you for gain. Malicious actors looking to benefit financially from personal data have grown in number and become more sophisticated as time has passed.
Cybercriminals often target both individuals and businesses in the same way. The most common form of attack is called phishing (note that this is unrelated to a beloved Vermont band). Phishing involves communication that seeks to obtain sensitive data. This communication is designed to look like it is coming from a legitimate source. However, upon close inspection, cracks may begin to form in the facade. For example, you may get an email from what appears to be your local bank, asking you to click a link and re-enter account information due to a payment that was declined. In addition, there is almost always some urgency to the request (e.g., your account will be charged a declined transaction fee if you do not respond within 24 hours). The key to not falling victim to these schemes is to read through the communication closely and reach out to the organization or individual to verify authenticity. The best way to do this is by looking up the organization or individual’s contact information from your records or via an online search. Do not use the phone number or email provided in the suspicious communication!
Another popular attack method involves installing malicious software (malware) on your computer. Cybercriminals will often accomplish this in the same manner as the fake emails mentioned previously, seeking to have the victim click on a nefarious link that allows the virus to gain access. Once inside your computer, the software can log data, delete information, or even lock down files for ransom. As you can imagine, having your entire system held for ransom is not a pleasant experience for individuals or organizations.
So what can you do as an individual to protect your data? Here are a few key steps:
- Always remain vigilant – be suspicious of all emails that seem out of context or warn of impending doom.
- Use strong passwords – rely on password strength indicators and use more complex passwords when possible.
- Keep your data close to the vest – be discerning about when and where you share your data.
Here at Hanson + Doremus, we work with an outside IT provider to make sure we are keeping client data as safe as possible. We have an internal Cybersecurity Policy with a number of different protective measures in place. We also have employees complete cybersecurity training and are constantly sharing reminders of best practices. Finally, we review all vendor relationships with an eye to security.
The unfortunate reality is that cybercrime is here to stay for the long haul, so we must all figure out ways to protect our information and systems. The good news is that awareness and engagement is at an all-time high and many resources are being put toward ensuring protection for both individuals and businesses.